How to use Active Directory and Specifying Printers to Specific Workstations
I was handed a project that could easily of been fixed by a really long usb cable (50 - 100 ft) but for flexibility of the physical devices it was better to look at a network based solution for managing the printer. However there are a couple caveats about the situation with the printer and the workstation requiring access.
- The network printer is on a completely different network then the workstation
- The workstation is on a managed domain
- We only want the one workstation to have access to the printer on the domain
- Power location is a problem
- Network location is a problem
The printer is on a network that is 172.31.x.x and has a IP reserved via PFSense firewall, the workstation is on a 192.168.x.x network on an Active Directory Domain that is assigned via DHCP and the network is controlled by a different PFSense firewall.
Now I realize that I could setup a route in the firewall to the printer allowing the domain account to access the printer, but to keep the complexity down on the firewalls (and that we would have to do a failover to make appropriate rule changes on our failover firewall) we decided not to add routes to the printer. I did have a virtual machine (not on the domain but in a workgroup) which was being used as a print release station with software from Envisionware for print and release printing from public workstations. The public workstations are just in a workgroup and on a 172.31.x.x network and our staff network is on a 192.168.x.x network. Our staff however can remote into the print release workstation to release jobs etc so it seemed to be the most elegant solution.
Step 1 - Make sure your print server is prepped.

Once the printer is shared out we use the Additional Drivers feature to add our 32 and 64 bit drivers so when our clients connect they know what driver to use and if they don't have it it automatically installs it if they have the proper permissions.

 |
| 32 and 64 bit drivers ready to automatically install |
STEP 2 - Setup your OUs and Group Policies
So as you can see in the image below I have a ROOT GP Policy, an OU called Group1 with a Group 1 GP and an OU called Workstation with a GP called LocalPrinter. I have other GP settings which are applied on a global basis and I am using OUs to have a greater finite control of what Group Policies I want to apply which is why this policy is three levels down. In this case the GP settings I want to have finite control over is the printer we just shared. I only want this printer to show up on this workstation when the user login and remove it when they logout.
 |
| Group Policy Management |
So we put our Workstation (Public1) in the workstation OU, and we apply the following GP settings
User Configuration -> Policies -> Windows Settings -> Scripts
 |
| Create Powershell Script in the Login/Logoff |
When you get the properties of the logon script you want to select the powershell tab and hit add
Script Name: Add Workstation Printer
Script Parameter:
Add-Printer - ConnectionName \\Reference01\CRC Printer
 |
| Powershell Script for adding the printer in GP |
and similarly we want to do the same thing to remove the printer from the user profile if they roam to another machine. So the logoff powershell script is the same with the Remove Switch instead of the Add
Script Name: Remove Workstation Printer
Script Parameter:
Remove-Printer - ConnectionName \\Reference01\CRC Printer
STEP 3 - Add the Shared Printer to Active Directory Print Management
Now that we have our GP and OUs all setup we can move forward and add the printer to our AD Printer Management Server. We want to add the Workstation Printer Server to work with our AD. Right click on print management and select add/remove servers
 |
| Server 2012R2 AD Print Management |
 |
| Add the shared printer from the Workstation |
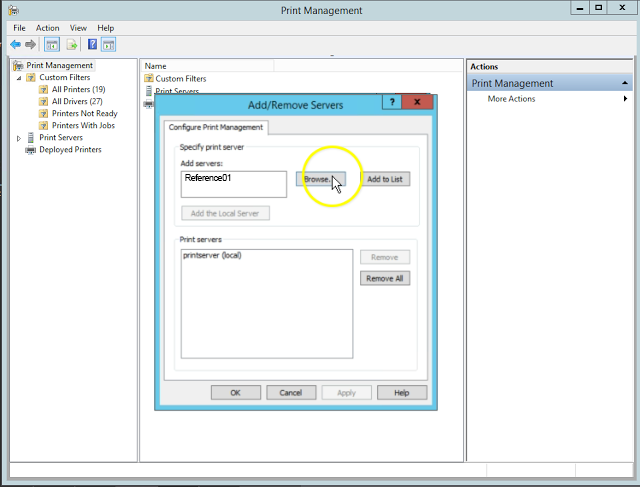 |
| Browse/Add the new workstation printer (Reference01) |
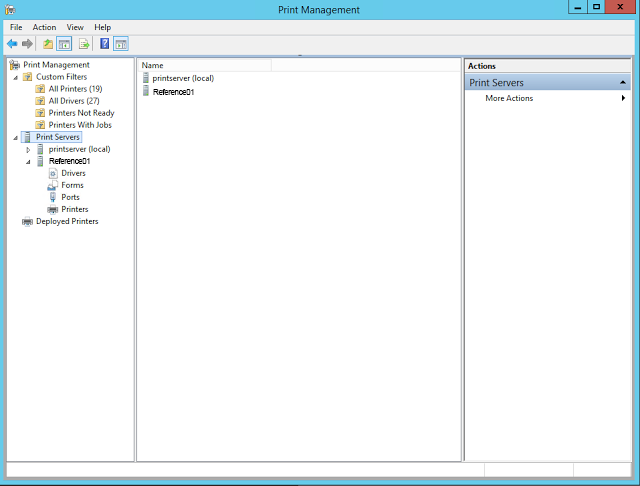 |
| List of Print Servers |
 |
| Deploy with Group Policy |
 |
| Deploy with Group Policy Settings |
 |
| A successfully deployed printer |
A successfully deployed printer via AD using OUs and GPs. All users should have no problem connecting on that machine with the current GP settings we have setup unless you have other restrictions in your group policy.
STEP 4 - Test and Verify.
Always best practice to test and verify anything you do and works the way you expect.